

Security Affairs
E-prescription provider MediSecure impacted by a ransomware attack
Electronic prescription provider MediSecure in Australia suffered a ransomware attack likely originate from a third-party vendor.


Security Affairs
Electronic prescription provider MediSecure in Australia suffered a ransomware attack likely originate from a third-party vendor.


Bleeping Computer
Electronic prescription provider MediSecure in Australia has shut down its website and phone lines following a ransomware attack believed to originate from a third-party vendor.

%20(1)%20(1).webp)
Cyber Security News
A newly disclosed vulnerability, identified as CVE-2024-22026, has been found in Ivanti EPMM, formerly known as MobileIron Core.


Latest Hacking News
Researchers caught numerous security vulnerabilities riddling Cinterion cellular modems, exploiting which would threaten millions of devices. Since no active patches currently exist for the flaws, the researchers recommend applying the suggested mitigations to prevent potential


Cyber Security News
Three vulnerabilities have been discovered in SAP Customer Experience (CX) commerce cloud and SAP Netweaver Application which were


Trend Micro
This report describes how Waterbear and Deuterbear — two of the tools in Earth Hundun's arsenal — operate, based on a campaign from 2024.


Ars Technica
Google's video synthesis model creates minute-long 1080p videos from written prompts.


Infosecurity News
CPR said exploit builders in .NET and Python have been employed to deploy this malware


The Hacker News
CVSS v4.0 evaluates vulnerabilities using a revised scoring system, emphasizing environmental and threat metrics.


Cyber Security News
Best Network Security Providers for the Healthcare Industry - 1. Perimeter 81, 2. Palo Alto Networks, 3. Fortinet, 4. Cisco, 5. Trend Micro


SecurityWeek
SAP has released 14 new and three updated security notes on its May 2024 Security Patch Day, including for critical vulnerabilities.


The Cyber Express
A threat actor using the alias qpwomsx has claimed responsibility for an alleged data breach affecting the popular Indian online


The Hacker News
Advanced authentication: The key to addressing the weakest link in cybersecurity - human users. Learn how to fortify your organization's defenses.


Cyber Security News
Few Critical vulnerabilities have been discovered in Cinterion Cellular modems that could allow an unauthorized remote attacker to execute


Bleeping Computer
A cybercriminal using the name "salfetka" claims to be selling the source code of INC Ransom, a ransomware-as-a-service (RaaS) operation launched in August 2023.


HACKRead
Kaspersky researchers have identified multiple security vulnerabilities in Cinterion cellular modems, which could be exploited by threat actors.


Infosecurity News
The flaws include CVE-2023-47610, a security weakness within the modem’s SUPL message handlers


SecurityWeek
A critical vulnerability in the Cinterion cellular modems can be exploited for remote code execution via SMS messages.


The Hacker News
Kaspersky researchers have uncovered multiple security flaws in Cinterion cellular modems that could put your communication networks and IoT devices a


The Cyber Express
An unidentified threat actor known as "pwns3c" has offered access to a database purported to contain sensitive data and documents


The Cyber Express
This week on TCE Cyberwatch we’re covering the different data breaches and vulnerabilities faced by different companies. Along with this,


Security Affairs
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs are free for you.

The Hacker News
The notorious FIN7 hacking group is at it again! This time, they're using malicious Google ads to trick users into downloading malware disguised as le


DarkReading
Researchers discovered seven vulnerabilities — including an unauthenticated RCE issue — in widely deployed Telit Cinterion modems.


The Hacker News
EDR solutions can detect threats that traditional defenses like antivirus often miss. Find out how EDR provides a deeper level of security.


Bleeping Computer
Security flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS.


Bleeping Computer
Security flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS.


Security Affairs
Citrix urges customers to manually address a PuTTY SSH client flaw that could allow attackers to steal a XenCenter admin's private SSH key.


Infosecurity News
Afghanistan, Turkmenistan and Tajikistan victims experienced the highest share of banking Trojans


The Hacker News
Russia-Linked APT28 Strikes Poland with Malware Campaign Polish government bodies were hit by a sophisticated malware attack orchestrated by the infam


The Hacker News
Looking to grow your MSP business? Consider offering vCISO services to meet the critical needs of SMEs. It’s a game changer for recurring revenue and


Infosecurity News
Researchers discover 75,000+ domains hosting fraudulent e-commerce sites, in a campaign dubbed BogusBazaar


The Cyber Express
IntelBroker has claimed the SigningHub data leak, impacting the UK-based online document signing and digital signature creation service provider. The


DarkReading
Instead of building a list of users and identifying what systems each use can access, Token Security starts with a list of machines and determining who can access each system.


CyberNews
Passport e-gates across the country temporarily stopped working, preventing travelers from boarding their flights.


The Cyber Express
The Hong Kong fire department uncovered a recent breach in its computer system that exposed the personal information of over


The Hacker News
UK's National Crime Agency has unmasked the admin behind the prolific LockBit ransomware as 31-year-old Russian national Dmitry Khoroshev.


CyberNews
OpenAI has said that it’s building a tool to detect content created by its text-to-image generator DALL-E 3, with early testing showing 98% accuracy.


CyberNews
The leadership identity of the LockBit ransomware group is unveiled by the US Department of Justice (DoJ), UK’s National Crime Agency (NCA), and Europol.


The Hacker News
Learn how Reflectiz detected a sophisticated malware hidden in an innocent-looking image on a retail site.


Infosecurity News
Russian national Alexander Vinnik has pleaded guilty to his role in a multibillion-dollar money laundering conspiracy


The Hacker News
Russian operator of BTC-e crypto exchange pleads guilty to money laundering charges spanning 2011-2017.


Security Affairs
Alexander Vinnik, a Russian operator of virtual currency exchange BTC-e pleaded guilty to participating in a money laundering scheme.


HACKRead
Cybersecurity researchers from Mac security provider, Kandji, have discovered a new malware dubbed "Cuckoo" targeting macOS users.

.webp)
Cyber Security News
Cybersecurity researchers have uncovered a new malware strain dubbed "Cuckoo., exhibits characteristics of both spyware and an infostealer


CyberNews
Arm and Intel-based Macs are being targeted by a new dangerous malware, dubbed Cuckoo.


CyberNews
Alexander Vinnik, a Russian cybercrime kingpin who was arrested in Greece in 2017, convicted of money laundering in France, and is now awaiting trial in California


The Hacker News
A new malware called "Cuckoo" is on the loose, targeting both Intel and ARM-based Macs.


The Record
Alexander Vinnik oversaw an operation that processed $9 billion in transactions, many of them allowing cybercriminals to transfer, launder and store the proceeds of their illegal activities.

.png)
Cyber Security News
The weekly news summary keeps you up to date with what’s happening in cybersecurity, including developments, vulnerabilities, breaches, threats, and defensive strategies. Knowing about new cyber risks and attack vectors helps you put up safeguards and preventive measures as soon as possible to protect your systems. Remaining constantly aware gives you a holistic view of […]


Security Affairs
The Blackbasta extortion group claimed responsibility for the attack that in April severely impacted the operations of Synlab Italia.

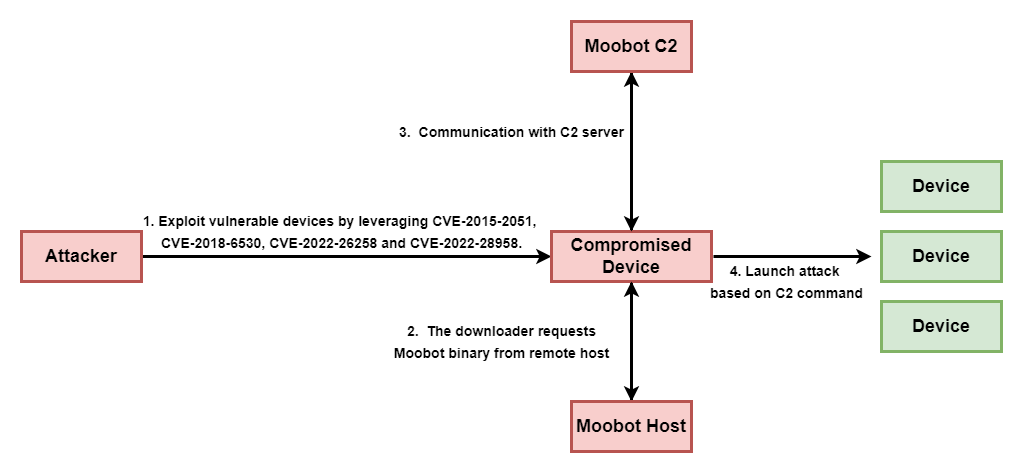
Security Affairs
The Ubiquiti EdgeRouter botnet is still used by Russia-linked group APT28 and cybercriminals organizations.


Cyber Security News
Solutions for each challenge are explained in more depth by Cynet’s new guide, “Top 10 Cybersecurity Challenges Faced by K-12 Institutions.”


DarkReading
Threat actor dropped in to Dropbox Sign production environment and accessed emails, passwords, and other PII, along with APIs, OAuth, and MFA info.


Security Affairs
Threat actors breached the Dropbox Sign production environment and accessed customer email addresses and hashed passwords


SecurityWeek
Network detection and response (NDR) provider Corelight has raised $150 million in a Series D funding round led by Accel.


DarkReading
DMARC adoption is more important than ever following Google's and Yahoo's latest mandates for large email senders. This Tech Tip outlines what needs to be done to enable DMARC on your domain.


CyberSecurity Dive
An attacker intruded the electronic signature platform’s production environment and accessed a trove of user data, including OAuth tokens.

.webp)
Cyber Security News
A new variant of the notorious Adload malware has been discovered to bypass the latest updates to Apple's built-in antivirus, XProtect.


The Cyber Express
Over a million Australians who frequented pubs and clubs have likely had their critical information exposed in Outabox data breach,


The Hacker News
Dropbox Sign Breached! Unidentified hackers accessed user emails, usernames, and account settings for all Dropbox Sign users.


SecurityWeek
Dropbox says hackers breached its Sign production environment and accessed customer email addresses and hashed passwords.


DarkReading
A recent campaign targeting Middle Eastern government organizations plays standard detection tools like a fiddle. Cyber defenders must keep pace.


CSO
The names and email addresses of those customers were also exposed who had never created an account with Dropbox Sign but had “received or signed a document through Dropbox Sign.”


Cyber Security News
Dropbox disclosed a significant security breach affecting its electronic signature service, Dropbox Sign (formerly known as HelloSign).


SecurityWeek
Police say a principal from a Maryland high school was framed as racist by a fake recording of his voice using AI-based deepfake technology.


SC Magazine
Security pros see the Dropbox Sign breach as not just a blow to Dropbox, but a really bad day for electronic signatures.


DarkReading
Unmanaged and unknown Web services endpoints are just some of the challenges organizations must address to improve API security.


Ars Technica
Easy-to-use language that drove Apple, TRS-80, IBM, and Commodore PCs debuted in 1964.


SecurityWeek
Chinese cybersecurity firm QAX XLab uncovered an Android trojan that hides its command-and-control server behind compromised WordPress sites.


Latest Hacking News
A security researcher discovered a security vulnerability in the Judge0 system, which received a patch that could further be bypassed, leading to further vulnerabilities. While the developer eventually patched the issue after repeated exploits, the


The Record
The company told federal regulators that it discovered unauthorized access to the production environment of its Dropbox Sign product.


Trend Micro
This blog entry aims to highlight the dangers of internet-facing routers and elaborate on Pawn Storm's exploitation of EdgeRouters, complementing the FBI's advisory from February 27, 2024.


Ars Technica
145,152-core supercomputer was 20th most powerful in the world in 2016.


DarkReading
The purported metadata for each these containers had embedded links to malicious files.


Bleeping Computer
Don't miss your chance to get The 2024 Cybersecurity Mastermind Training Bundle on sale for just $39.99 (reg. $300).


Bleeping Computer
A new Android backdoor malware named 'Wpeeper' has been spotted in at least two unofficial app stores mimicking the Uptodown App Store, a popular third-party app store for Android devices with over 220 million downloads.


The Hacker News
Millions of malicious "imageless" containers have been planted on Docker Hub over the past 5 years in multiple cybercriminal campaigns.

.webp)
Cyber Security News
This sophisticated backdoor Trojan to infiltrate Android systems & execute a malicious commands, posing a threat to unsuspecting users.


CSO
In the written testimony before the House Energy and Commerce Committee, CEO Andrew Witty said after gaining access, the threat actor moved laterally within the systems using sophisticated methods and exfiltrated data.


Bleeping Computer
Google blocked 2.28 million Android apps from being published on Google Play after finding various policy violations that could threaten user's security.


Bleeping Computer
Google blocked 2.28 million apps from being published on Google Play after finding various policy violations that could threaten the security of Android users.


The Cyber Express
Okta reported an "unprecedented scale" of credential stuffing attacks targeting its identity and access management solutions, resulting in the breach


Bleeping Computer
The All-in-One Super-Sized Ethical Hacking Bundle is on sale for just $45.99 (reg. $1098) for a limited time only.


The Hacker News
Multiple vulnerabilities have been discovered in the popular Judge0 online code execution system, putting users at risk of complete system compromise.


Security Affairs
Los Angeles County Department of Health Services reported a data breach that exposed thousands of patients' personal and health information.

The DFIR Report
Key Takeaways In August 2023, we observed an intrusion that started with a phishing campaign using PrometheusTDS to distribute IcedID. IcedID dropped and executed a Cobalt Strike beacon, which was … Read More


The Record
Ukraine’s government uses the bots to collect and share real-time information about Russian military activity.


The Record
The CEO of one of the largest banks in the world discusses cryptocurrency and artificial intelligence, as well as how he's been able to influence cybersecurity culture.

Cyber Security News
Hackers abuse the Autodesk hosting platform to host malicious PDF files, which leads to phishing attacks on victims.


The Cyber Express
Volkswagen, the automotive giant, finds itself at the center of a large-scale cyber operation, with suspicions pointing toward hackers operating


DarkReading
The payment card industry pushes for more security in financial transactions to help combat increasing fraud in the region.


Bleeping Computer
The Los Angeles County Department of Health Services disclosed a data breach after thousands of patients' personal and health information was exposed in a data breach resulting from a recent phishing attack impacting over two dozen employees.


Bleeping Computer
The L.A. County's Department of Health Services, the second-largest public health care system in the United States, disclosed a data breach after patients' personal and health information was exposed in a data breach resulting from a recent phishing attack impacting over two dozen employees.


DarkReading
Mobile malware-as-a-service operators are upping their game by automatically churning out hundreds of unique samples on a whim.


HACKRead
Modern cybersecurity uses the concept of Network Detection and Response (NDR) as an active approach to fortifying defences against threats.


SecurityWeek
A new phishing campaign abuses compromised email accounts and targets corporate users with PDF files hosted on Autodesk Drive.


Bleeping Computer
From CISA to CISSP, you can also find training and exam prep for the certifications that employees desire. Get lifetime access to all three IT and cybersecurity e-learning platforms for $119.99 (reg. $480).


SecurityWeek
Zero trust endpoint security company ThreatLocker has announced a $115 million Series D funding round that brings the total to $240 million.


Infosecurity News
The US Treasury announced sanctions on two companies and four individuals for cyber campaigns conducted on behalf of the Iranian government
Loading more articles....